Protecting Your Digital Landscape
Comprehensive Cybersecurity Solutions
Empowering public sector and enterprise organizations with tailored cybersecurity services to safeguard sensitive data and ensure compliance.
Cybersecurity Solutions
Focusing on various security measures and tools that protect data, networks, and systems from cyber-attacks and vulnerabilities.







Data Security & Privacy
Protecting sensitive data from unauthorized access and ensuring compliance with privacy regulations.
Cloud Security
Safeguarding cloud-based data, applications, and infrastructure against cyber threats.
Application Security
Securing software applications by identifying and mitigating vulnerabilities during development and deployment.
Browser Security
Defending web browsers and their interactions from malicious websites, plugins, and data breaches.
Email Security
Protecting email communications from phishing, malware, and unauthorized access.
Endpoint Security
Securing devices like laptops, desktops, and mobile devices from cyberattacks and data loss.
Network & Infrastructure Security
Protecting networks and physical infrastructure from intrusions, data leaks, and attacks.
Operational Technology Security
Securing operational technology systems like industrial control systems (ICS) and SCADA from cyber threats.
Identity & Access Mgmt. (IAM)
Managing and securing digital identities and ensuring only authorized users have access to critical systems.
Risk Management & Response
Managing risk, ensuring compliance, and responding to security incidents.



Governance, Risk & Compliance (GRC)
Managing and aligning security practices with regulatory requirements while mitigating risks across the organization.
Incident Response (IR) & Threat Intelligence (TI)
Detecting, responding to, and mitigating security incidents using real-time threat intelligence.
Vulnerability Management & Penetration Testing
Identifying and addressing vulnerabilities through proactive scanning and simulated attacks to strengthen security defenses.
Managed & Professional Services
Ongoing managed services, staffing, and educational services that help clients maintain their security posture.
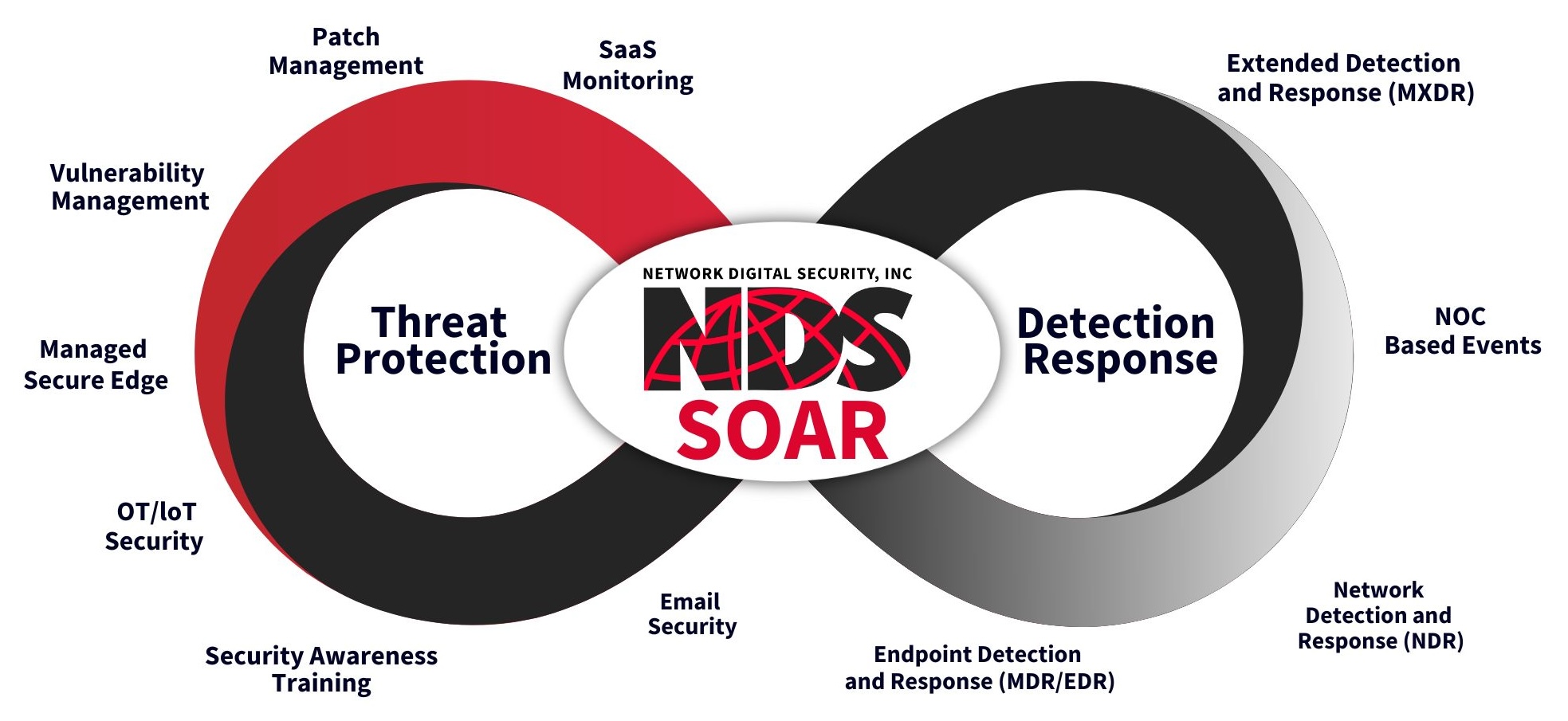
Managed Security Services
Providing continuous monitoring and management of security systems to protect against emerging threats.
Security Operations Center (SOC) Services
Offering centralized, real-time monitoring and incident response to detect and mitigate cybersecurity threats.
Staff Augmentation, vCIO, vCISO
Supplying expert security leadership and support through virtual CIO/CISO roles and skilled personnel to bolster security teams.
Security Awareness & Education
Educating employees and stakeholders on best practices to prevent security breaches and promote a security-first culture.
What Our Clients Say
Virtual Chief Information Officer Services (vCIO)
“When the Cobb County School District (CCSD) needed assistance from a technology advisory expert, we immediately thought of Jim Finger. His knowledge and experience in the ever-changing and ever-challenging technology environment ensured CCSD that we would receive the most up-to-date guidance regarding our specific technology issues.” — Chief Operating Officer
Red Team Pentest
“NDS provided the most comprehensive assessment of our cybersecurity risks.” — Chief Information Officer, Government facility.
Virtual Chief Information Officer Services (vCIO)
“In all of Mr. Finger’s activities I have found him to be professional in the manner he interacted, made presentations and provided recommendations. He displayed in-depth and broad technical knowledge that was respected by those who came in contact with him. The information that Mr. Finger provided could be trusted to be true, accurate and as current as possible. “ — Director, Technology Services, Top 20 largest School District.
Your Questions Answered
We understand that cybersecurity can be complex. Here are answers to some of the most common questions we receive from our SLED clients.
What is managed security and how can it benefit my organization?
Managed security involves outsourcing your cybersecurity needs to experts who monitor and manage your security systems 24/7. This ensures continuous protection and quick response to any threats, allowing your organization to focus on its core functions.
How does Network Digital Security ensure compliance with regulations like CJIS and FERPA?
Our team stays up-to-date with all relevant regulations and implements best practices to ensure your organization remains compliant. We conduct regular audits and provide detailed reports to help you meet all necessary standards.
What should I do if my organization experiences a cyber attack?
Contact our incident response team immediately. We will guide you through the necessary steps to mitigate the attack, recover data, and prevent future incidents. Our team is available 24/7 to assist you in any emergency.
Can you provide cybersecurity training for our staff?
Yes, we offer comprehensive cybersecurity training programs tailored to the needs of SLED organizations. Our training covers the latest threats, best practices, and compliance requirements to ensure your staff is well-prepared to handle cyber risks.
How do you protect sensitive data in transit and at rest?
We use advanced encryption techniques to protect your data both in transit and at rest. Our solutions ensure that sensitive information remains secure from unauthorized access, whether it is being transmitted over the network or stored on your servers.
What makes Network Digital Security different from other cybersecurity providers?
Our focus on the SLED market sets us apart. We understand the unique challenges faced by state, local, and educational institutions and provide tailored solutions to meet their specific needs. Our expertise in compliance and our proactive approach to security make us a trusted partner for many SLED organizations.
Secure Your Future Today
Don’t leave your cybersecurity to chance. Schedule a consultation with our experts to discuss tailored solutions that meet your unique needs. Protect your organization with Network Digital Security’s comprehensive services.